With Windows 2008 Microsoft introduce a new tool called Active Directory database mounting tool (Dsamain.exe) This was referred as Snapshot viewer and Active Directory data mining tool during the early release of the Windows 2008. The cool thing about this tool is you can take snapshots of your AD database and view it offline.
As for Microsoft explanation this is really helpful in Forest recovery and AD auditing purpose. In the case of AD objects deletion you can load a snapshot and compare your current AD alone with it.
Before the Windows Server 2008 operating system, when objects or organizational units (OUs) were accidentally deleted, the only way to determine exactly which objects were deleted was to restore data from backups. This pain behind this is:
- Active Directory had to be restarted in Directory Services Restore Mode to perform an authoritative restore.
- An administrator could not compare data in backups that were taken at different points in time (unless the backups were restored to various domain controllers, a process which is not feasible).
but one thing to notice is this is not a method to recover deleted objects but merely a method to show to you what has happened by doing a comparison. Apart from that you’ll need to be a member of the Enterprise admins or domain admins group, or else given particular rights for a user account.
Now getting back to the actions, to get snapshot, mount them and view them you need to know about 3 tools,
1. NTDSUTIL – Create, delete, mount, list the snapshot.
2. Dsamain.exe – This will allow us to expose snapshot to LDAP servers.
3. LDP or Active Directory Users and Computers MMC to view the mounted snapshot.
So the steps going to be as follows,
1. Manually or automatically create a snapshot of your AD DS or AD LDS database.
2. Mount the snapshot.
3. Expose the snapshot as an LDAP server.
4. Connect to the snapshot.
5. View data in the snapshot.
Manually creating the snapshot of the AD DS
1. Logon to a Windows Server 2008 domain controller.
2. Click Start, and then click Command Prompt.
3. In the Command Prompt window, type ntdsutil, and then hit Enter.
4. At the ntdsutil prompt, type snapshot, and then hit Enter.
5. At the snapshot prompt, type activate instance NTDS, and then hit Enter.
6. At the snapshot prompt, type create, and then hit Enter.
7. Note down the GUID return by the command.
Mount the snapshot
1. If you didn’t close the previous window just go for it again and type list all and press enter.
2. Once you get the list of the snapshots you can select a snapshot to mount. In this scenario type mount 2 and press enter.
3. If the mounting was successful, you will see Snapshot {GUID} mounted as PATH, where {GUID} is the GUID that corresponds to the snapshot, and PATH is the path where the snapshot was mounted.
4. Note down the path
Expose the snapshot as an LDAP server
Ok so far we manage to create a snapshot and mount it. Now we need to expose the snapshot so we can view it from LDP utility or by using ADUC mmc. In this scenario we’re going to use the second utility (Active Directory Users and Computers)
1. Open a new command prompt
2. In the Command Prompt window, type dsamain /dbpath C:\$SNAP_201001281107_VOLUMEC$\WINDOWS\NTDS\ntds.dit /ldapport 51389 (instead of using the default 389 port we’re using a alternative port the snapshot to minimize any conflicts with the live AD DS)
note: “C:\$SNAP_201001281107_VOLUMEC$” is the path we got few steps before and represent the snapshot mounted path in our system.
3. "Microsoft Active Directory Domain Services startup complete" will appear in the Command Prompt window after running the above command. This means the snapshot is exposed as an LDAP server, and you can proceed to access data on it. NOTE: Do not close the Command Prompt window or the snapshot will no longer be exposed as an LDAP server.
Connect to the snapshot
We can use any utility which can read the LDAP data. In this demonstration as I mention earlier I’ll go ahead and use the Active directory Users and Computers snappin.
1. Open the ADUC.
2. Right click the ADCU and select “Change domain controller” option.
3. Type the domain name with the custom port number eg “CONTOSO-DC:51389”
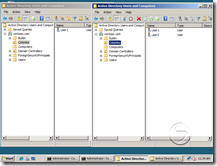
4. Now you’re looking at the data in the snapshot. Go ahead and open a another ADCU window and that will open the current AD DS.
5. Go ahead and do a change on the live AD DS and then check the 2 MMC’s again. You’ll see the snapshot data is not getting changed.
So as I mention this is really cool feature and saves lot of time. If you don’t like creating snapshots manually you can create a schedule task and automate this to create snapshot automatically. One concern is these snapshot are not encrypted so if this gets to wrong hand it is bad for you guys. So try to keep them in a safe location and try to encrypt them for added security.